API keys
Generate and manage API keys.
API keys are used for several actions in your Baseten workspace:
Deploying and managing models through the Baseten Python client
Invoking deployed models via HTTP requests
Invoking worklets via HTTP requests
In this doc, we'll cover the entire lifecycle of securely creating and using API keys.
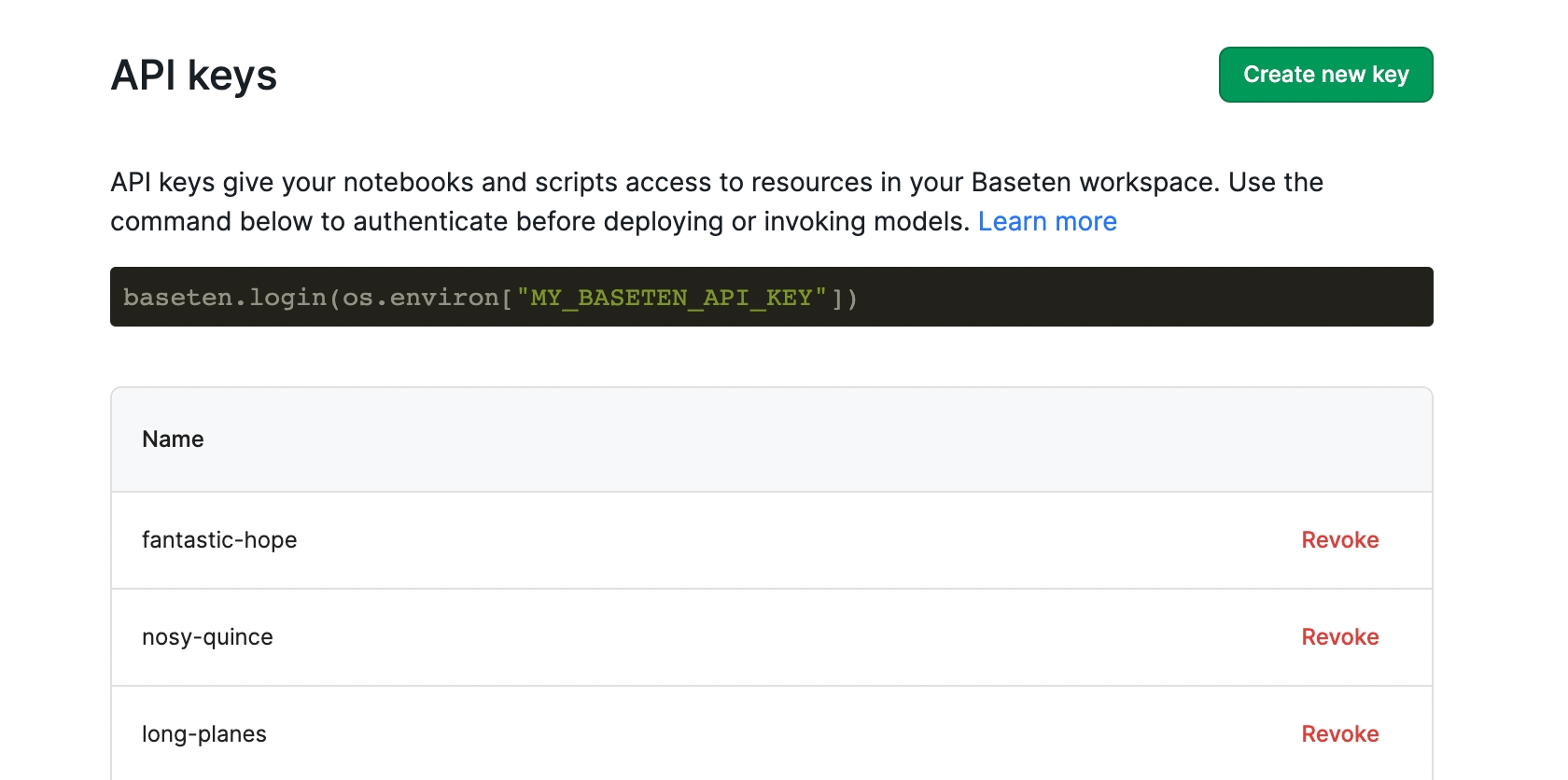
Creating API keys
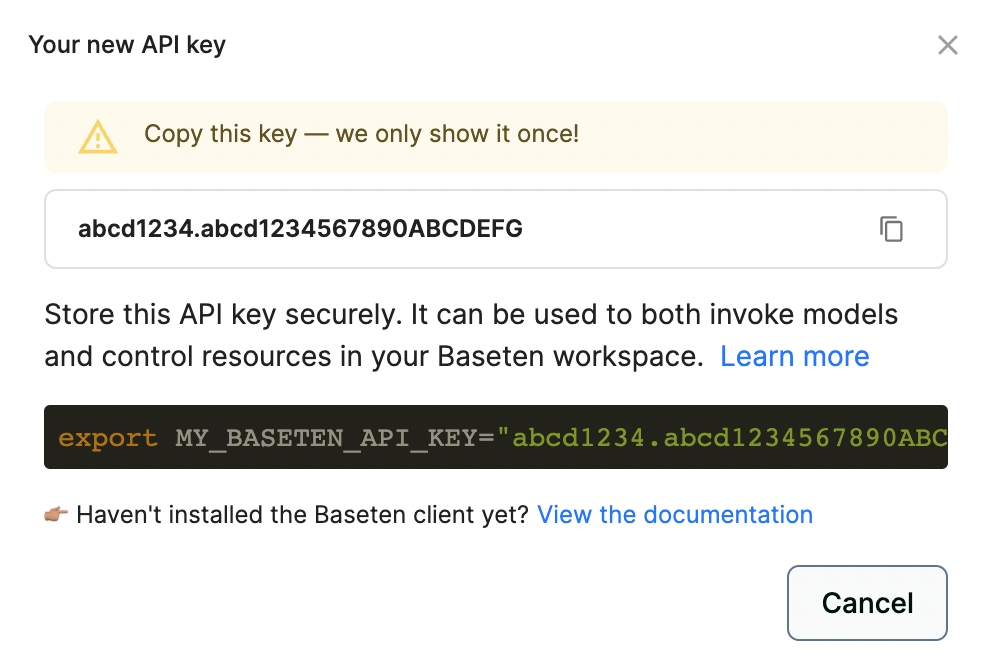
To create an API key, visit the "API keys" tab in your account settings. Click "Create new key" and a key will be generated for you. Make sure to copy the string displayed, you won't be able to access it again.
After your key is generated, it'll be shown on the "API keys" tab with a randomly generated two-word name.
You can revoke keys to remove access from your account at any time.
Using API keys
You can keep your Baseten account secure by guarding your API keys like passwords or other sensitive secrets.
The best way to keep your API key secure is to store it as an environment variable. You can set environment variables locally by adding the following to ~/.zshrc or whatever config file your system uses.
Then, in your Python code, add:
Here are some more tips for using API keys securely:
Never give your API key to anyone (they can create their own API key in their Baseten account on your workspace).
Never use your API key directly in the front-end of a web application where users could see it by inspecting the code in the browser.
Never store your API key in a file that is pushed to GitHub or another version-controlled repository
Never publish your API key with an iPython notebook.
Managing API keys
Make sure to keep your keys out of source code and version control. If you ever suspect a key has been leaked, promptly revoke it from your account and generate a new one. For more, see Google's recommended practices for securely using API keys.
Last updated